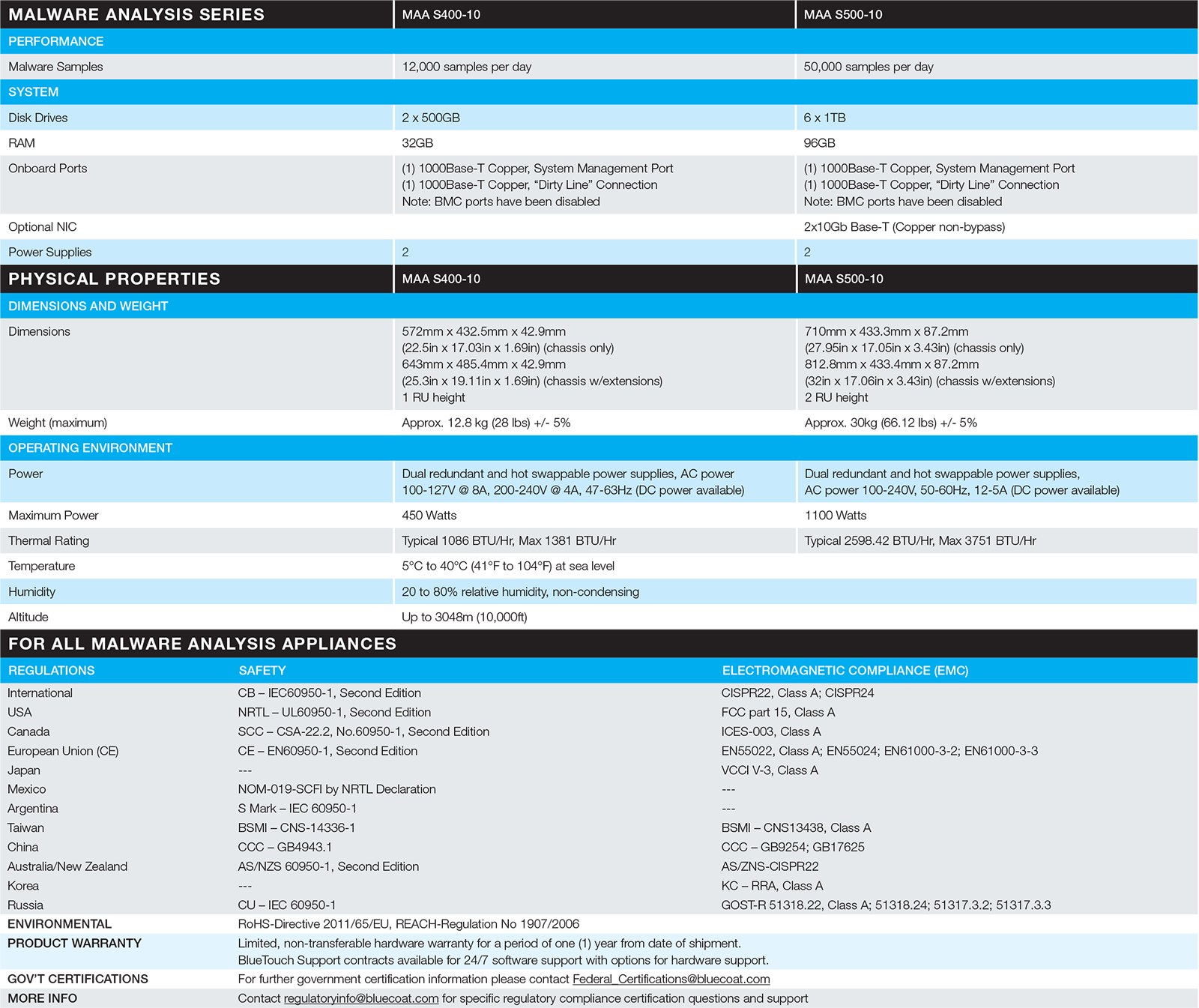
Malware Analysis S400/S500
Respond To Malicious Threats That Elude Traditional Defenses
Description
Detects and analyzes unknown, advanced, and targeted malware using a unique, dualdetection approach that safely detonates suspicious files and URLs, reveals malicious behavior, and exposes zero-day threats.
Capabilities
- Comprehensive, enterprise-class malware detonation in highly realistic sandbox environments
- Combines dynamic, static, and reputational analysis techniques for more thorough exposure of malware
- Scalable and customizable solution
- Detailed forensics and shared threat intelligence
- Seamless integration with Blue Coat Content Analysis, Blue Coat Mail Threat Defense or Blue Coat Security Analytics
Key Benefits
- Transforms malware exposure into continuous security improvement
- Superior detection, more accurate and relevant analysis
- Exceptional performance even on high-volume networks
- Helps prioritize and accelerate incident response
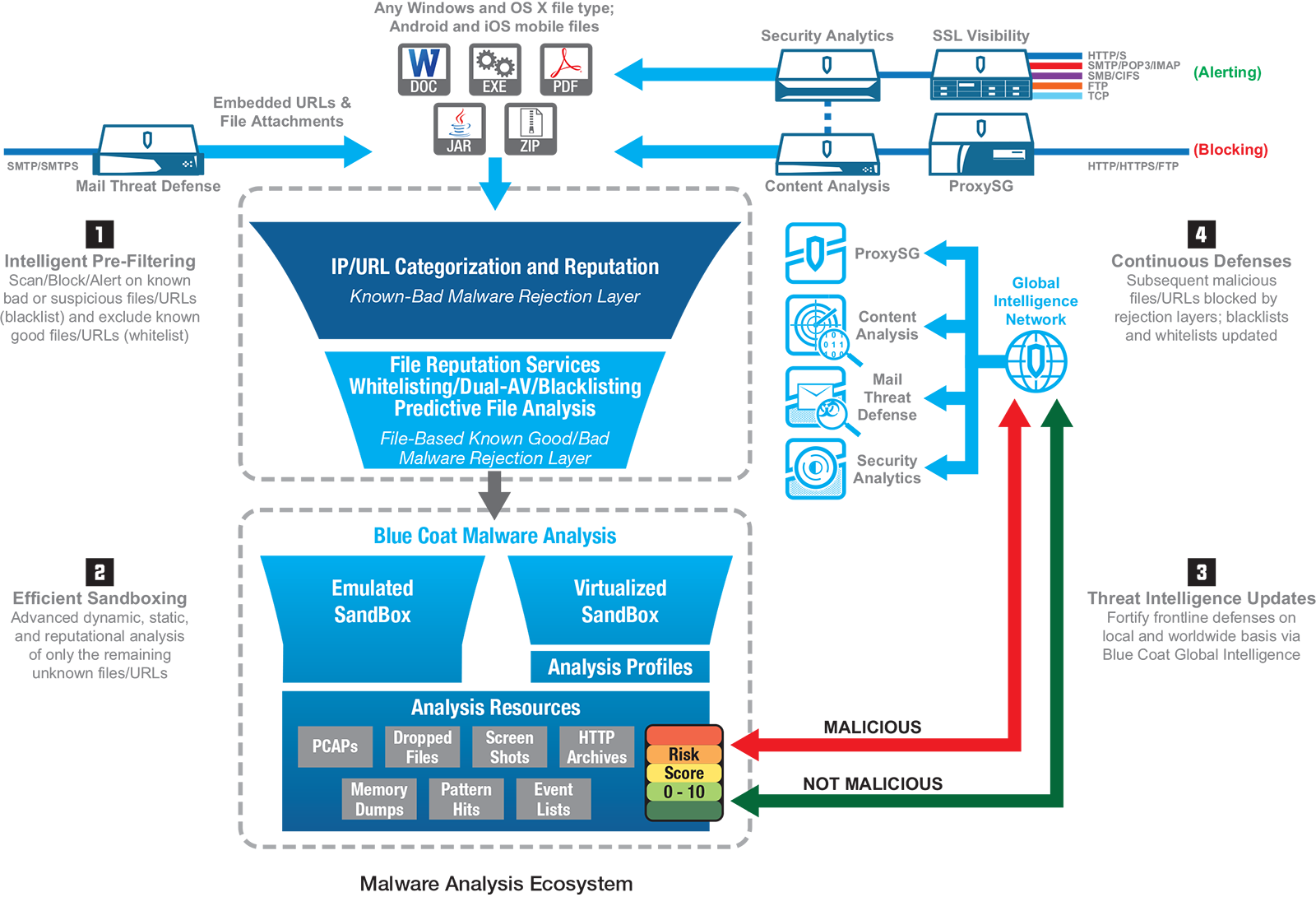
Blue Coat Malware Analysis is a key component of Blue Coat’s Advanced Threat Protection solution. Integrated with Blue Coat Content Analysis, Blue Coat Mail Threat Defense or Blue Coat Security Analytics, it provides a highly scalable solution for detecting and analyzing unknown, advanced, and targeted malware. This adaptive and customizable sandbox solution delivers enterprise-class, comprehensive malware detonation and analysis using a unique, dual-detection approach to quickly analyze suspicious files and URLs, interact with running malware to reveal its complete behavior, and expose zero-day threats and unknown malware.
Expose More Malicious Behavior
Malware Analysis utilizes a powerful dual-detection approach that combines virtualization and emulation to capture more malicious behavior across a wider range of custom environments than typical consolidated single-sandbox solutions.
- • Emulation Sandbox: An instrumented, fully controlled, replicated PC computing environment emulates Windows systemsto detect malware that otherwise will not detonate within a virtualized environment
- • Virtualization Sandbox: Custom analysis profiles replicate actual Windows production environments, down to the applications and versions in use, to quickly spot anomalies and behavioral differences that unveil anti-analysis, sleep, and other advanced evasion techniques. A virtualized Android sandbox detects and analyzes mobile threats traversing enterprise networks.
Multiple Detection Techniques
Malware Analysis uses a combination of static and dynamic analysis techniques that employ standard, custom, and open source YARA patterns to unmask cleverly disguised malware. It detects packed malware and VM-aware samples that alter their behavior in an artificial environment, plus malware that attempts to wait out any sandbox analysis using short or long sleeps.
Defeat Anti-Analysis at Many Levels
Anti-analysis defeating tools – such as hookbased introspection, high-level and low-level event capture, and detection in both kernel and user modes – intercept and convert behavior into detailed forensic intelligence.
Interact with Running Malware
A flexible plug-in architecture extends detection and processing by interacting with running malware, clicking through dialog boxes and installers, and generating unique post-processing analysis artifacts.
Generate More Relevant Results
Virtual machine profiles replicate multiple custom production environments, allowing security analysts to analyze threats across a range of operating systems and applications. They can closely match their organizations’ desktop environments, gathering intelligence on malware targeting their organizations directly or seeking to exploit specific application vulnerabilities.
Customize Detection and Risk Scoring
Detection criteria, analysis parameters, firewall settings, and risk scoring can all be customized to add flexibility, unique detection, and fast response capabilities when analyzing non-traditional and targeted malware in unique production environments.
Adaptive Intelligence for Changing Threats
Since Malware Analysis does not rely on static signatures, its flexible detection patterns are designed to detect polymorphic files, singleuse targeted malware, and fast-changing website domains.
Detailed Forensics for Remediation
Blue Coat sandboxing technology provides security defenders a comprehensive map of the damage – including both host-based and network indicators of compromise – that any malicious file or URL would cause to equivalently configured production machines without putting actual computers or sensitive data at risk.
Share Threat Intelligence
As unknown, advanced, or targeted malware and zero-day threats are exposed, the previously unseen or uncategorized threats are shared across the security infrastructure with the Blue Coat Global Intelligent Network, a network effect of our 15,000 customers worldwide.
Inoculation for Forward Defenses
Malware Analysis turns unknown threats into known threats and shares threat data with others across the global network, improving the effectiveness of front-line defenses such as Blue Coat ProxySG secure web gateways by moving protection forward to the perimeter where blocking will take place for subsequent attacks.
Malware Analysis Features
- Dual-detection emulated and virtual sandbox analysis environments
- Customizable Windows 8/7/XP profiles closely match production systems
- Virtualized Android sandbox detects mobile threats
- Pattern-based detection exposes malicious files and URLs including polymorphic, unique, and targeted threats
- Supports any PC file format
- Clicks through dialogs and installers to expose interactive malware requiring user interaction
- Thwarts VM-aware malware, bypasses sleep calls, and detects generic exploits such as “heap sprays”
- Customizable pattern matching, analysis settings, and risk scores
- Automatic pattern updates for continuous protection against fast-evolving threats
- Generates relevant, granular verdicts plus a complete range of analysis artifacts
- Seamlessly integrates with Blue Coat Content Mail Threat Defense and Security Analytics
- Integrates with the Global Intelligence Network for continuous threat sharing among our 15,000 customers who include over 70% of the Fortune Global 500
- Supports centralized appliance management for enterprise provisioning and deployment
- Provides real-time sandboxing to block malicious files before delivery
Malware Analysis Benefits
- Superior threat detection: Unique dualdetection approach combines emulation and virtual sandboxing, plus static and dynamic analysis techniques, to deliver unrivaled intelligence for unknown threats
- Accurate and relevant analysis: Customized virtual machine profiles running Windows XP, Windows 7, and Windows 8 closely replicate actual corporate gold images to detect targeted threats against actual production configurations
- Customizable analysis and risk scoring: Automatic sample classification and risk scoring – augmented by custom detection patterns, interactive analysis plugins, and risk scores – flag suspicious system events based on degree of potential malicious activity within your unique environment
- High throughput performance: Parallel sample processing on up to 55 virtual machines per single Malware Analysis appliance generates continuous enterpriseclass performance on high volume, high threat networks
- Improved incident response: Helps prioritize and focus incident response, streamlining damage assessments and speeding remediation efforts
- Inoculates forward defenses: Shares threat intelligence with the Global Intelligence Network, providing rapid updates to inline forward defenses that quickly block newly exposed malware